Writeup - Postmaster (ASVCTF 2022)
ASVCTF 2022 - Postmaster Writeup
- Type - Web
- Name - Postmaster
- Points - 300
Description
1 | Now introducing: email-based flag delivery. |
Writeup
Accessing the site revealed another simple page:
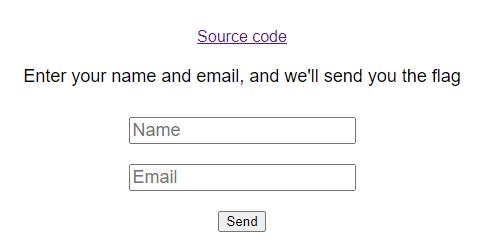
Clicking on the link to Source revealed the source code, found here. The important part is this:
1 |
|
The gist is that sending a POST request to the /send_email endpoint with two parameters, name and email, will cause the system to send an email through an SMTP server to the email address specified with the name attached. To get the flag, the email needs to be set to [email protected] - the problem is, if that’s the email, then we will never see the flag since we don’t own that email.
Upon closer inspection, one line stands out - mail['To'] = name + ' <' + email_address + '>'. The name and email_address parameters are piped directly into “To” SMTP header, and the only validation on name is no newlines (/n, /r). This means we can insert a name such as Test <[email protected]> and then the email as [email protected], making the “To” line Test <[email protected]> <[email protected]>. This will send the email to us, but the email parameter will still give us the flag.
Solve Script
Here is my automated exploit in Python:
1 | import requests |
Email I received (in my spam folder):
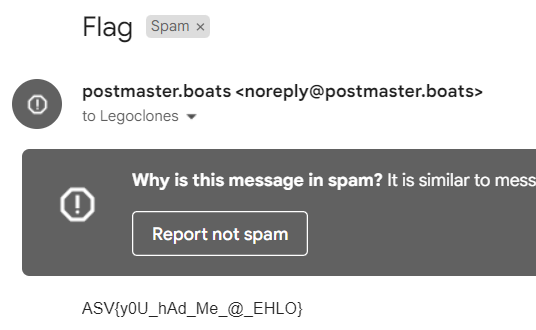
Flag: ASV{y0U_hAd_Me_@_EHLO}